SFTP (SSH File Transfer Protocol) is a secure file transfer protocol runs over the SSH protocol. It supports the full security and authentication functionality of SSH.
SFTP has replaced legacy FTP as a file transfer protocol provides all the functionality with security and reliability.
SFTP also protects against password sniffing and man-in-the-middle attacks. It protects the integrity of the data using encryption and cryptographic hash functions, and authenticates both the server and the user.
OpenSSH Installation using .zip file
- Goto https://github.com/PowerShell/Win32-OpenSSH/releases
- Download the OpenSSH-Win64.zip file from the latest release
- Extract the zip file contents to the folder C:\Program Files\OpenSSH
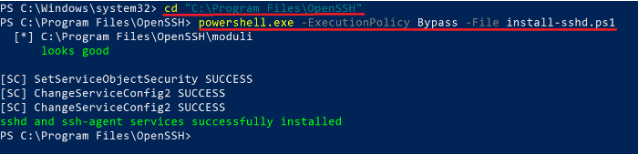
- Open a command prompt as Administrator and use the following command to change to openssh directory
- cd "C:\Program Files\OpenSSH"
- Run the following command
- Now the sshd and ssh-agent windows services should be installed. This can be seen in the services.msc window
- Change the startup type to Automatic from Manual and start both the services. Since we have set the startup type as automatic, both the services will start automatically upon system startup.
- Create the appropriate firewall policy to expose the SFTP port 22 to local or remote systems if required
- Now SFTP server accepts connections using username and password authentication
Setup SFTP server in newer versions of windows
- Click windows button and search for “manage optional features”
- Click on “add a feature” and search for OpenSSH server and install it
- Now Open SSH server and OpenSSH Authentication agent services should be installed in the services.msc window
- You ca right click and change the start up type of both the services as automatic if you want the services to start upon system start up
- Create the appropriate firewall policy to expose the SFTP port 22 to local or remote systems if required
- Now SFTP server accepts connections using username and password authentication
Downsides of password based authentication in SFTP
- OS user credentials of the server operating system are to be shared with the SFTP client which is not desirable
- OS user password is to be changed to change the password of SFTP client
- OS user password will be transmitted over the network
Benefits of using public key based authentication in SFTP
- This type of authentication is more robust and secure
- SFTP client need not know the OS user password
- Multiple clients can use different private keys for a single OS user
- Private key can be changed easily from time to time without changing the user’s OS password
- Access of SFTP client can be easily revoked by just removing the client’s public key from the authenticated list, without locking out or modifying the OS user account
Setup public key based authentication in Linux
- Open a terminal window and run ssh-keygen command. Press enter till the execution is complete as shown in the image below
- During the key generation process, password protection can be set to private key by entering a passphrase as shown in the above image. This ensures additional protection in case the private key is in wrong hands
- The public key will be saved as /home/<username>/.ssh/id_rsa.pub (home directory of user and /root for root directory) and private key will be saved as /home/<username>/.ssh/id_rsa (home directory of user and /root for root directory)
Place the public key in the SFTP server
- Use following scp (secure copy) command to copy the public key in the server directory (The default directory is C:/ProgramDate/ssh) as shown in the screenshot
- scp .ssh/id_rsa.pub <username>@<sftp server ip or hostname>:/C:/ProgramData/scp
Copying Public Key in authorized_key
- Method 1 : If you have direct access to Windows Server, than open command prompt go to C:/ProgramData/ssh and use type command to copy/append the public key in administrators_authorized_key
- Method 2:
- If you don't have direct access to Windows Server than Login to server with SSH from Linux as shown below to copy the public key in administrators_authorized_key as shown bellow.
- After Entering the Password it will show the windows login as shown below screen shot
Change the Permission of the administrators_authorized_keys file using following command directly from
- Use following command to allow the access permission of administrators_authorized_key to only administrator and system users of windows operating system.
icacls administrators_authorized_keys /inheritance:r /grant "Administrators:F" /grant "SYSTEM:F"
- Goto Server C:/ProgramData/ssh folder open sshd_config file in notepad in admin mode and uncomment pubkeyAuthentication yes line and save the file.
- Restart the Openssh services and try to login without password from the Linux box
- Now you are able to login have complete access on User Home directory
- If you want to give access to specific folder, add following line at the of sshd_config file and restart the service.
- In this demonstration I have used SFTP_Root folder present in user home directory.
Match User <username>
ChrootDirectory ~/<directoryname>
X11Forwarding no
AllowTcpForwarding no
PermitTTY no
ForceCommand internal-sftp
PasswordAuthentication no
Method 1: Login to the sftp server and use get command to get the file as shown in the screenshot
Method 2: Directly download the file from the command prompt using sftp command as shown in the screenshot bellow